Welcome
Welcome
Hello and Welcome!
Be sure to attend our monthly meetings. Lots of good information there. ISC2CT.org **
Come Join our (ISC)2 Connecticut Chapter Discord Server
Upcoming events:
"CPE 2026 Cybersecurity Practitioners Event | Feb, 13 2026 | Mohegan Sun Casino Uncasville, CT Immerse yourself in a comprehensive day exploring the forefront of cybersecurity. An event for Practitioners and be sure to challenge yourself in the CTF. Registration Link
Cybersecurity Summit: Implications of AI | February 24, 2026 | Virtual On Demand Through February 27, 2026 Free to Attend In 2026, AI is more than a technology — it’s the new battleground for enterprise security, resilience, and strategic advantage. The Strategic AI Summit 2026 brings together senior leaders in cybersecurity, enterprise risk, infrastructure operations, AI governance, and digital trust — from industries like finance, healthcare, critical infrastructure, cloud & SaaS, manufacturing, telecom and government — to engage in a single-day, high-impact virtual event. Agenda & Registration Link
Thank you to our Sponsors
Quinnipiac University is committed to helping advance the field of cybersecurity through its School of Computing & Engineering. To support the growth of professionals within cybersecurity and computing, Quinnipiac offers flexible online and on-campus opportunities that deliver practical skills you can immediately apply on the job. Both its MS in Cybersecurity and MS in Computer Science programs feature hands-on experience in lab settings that simulate real-world scenarios. To learn more about these exciting opportunities, Visit Quinnipiac University ...
Cyber News

Microsoft Rushes Emergency Patch for Office Zero-Day
Microsoft has rushed out an emergency patch for a security vulnerability in multiple versions of Microsoft Office and Microsoft 365 that attackers are actively exploiting.
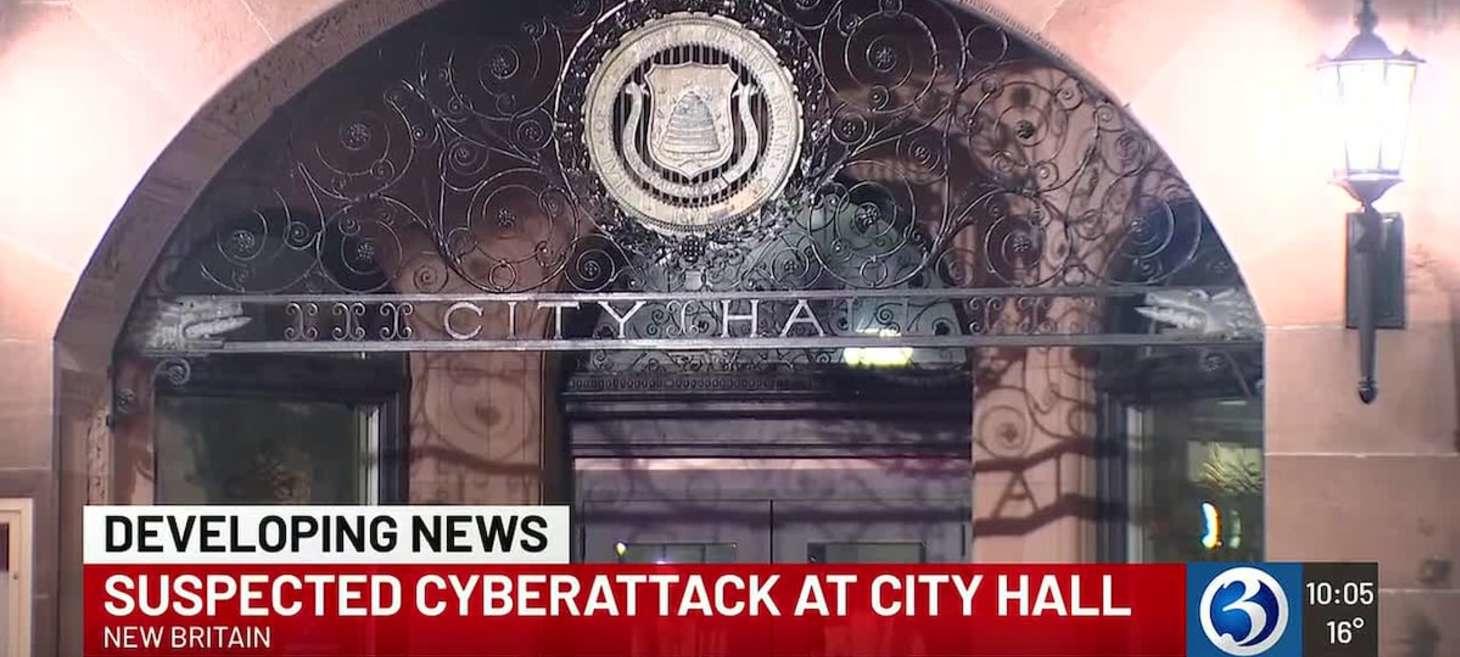
City of New Britain hit with a ransomware attack
New Britain officials confirmed that a ransomware attack knocked out internet access at City Hall.

WinRAR vulnerability still a go-to tool for hackers, Mandiant warns
APTs and financially motivated attackers continue leveraging WinRAR vulnerability (CVE-2025-8088) that's been fixed over half a year ago.

CISA Updates KEV Catalog with Four Actively Exploited Software Vulnerabilities
CISA added four actively exploited vulnerabilities to its KEV catalog, urging U.S. federal agencies to apply fixes by February 12, 2026.

Trump signs executive order for single national AI regulation standard, limiting power of states
President Trump's executive order, which limits the power of states in regulating AI, is a win for big tech companies that have lobbied for a federal standard.

Some AI apps leak loads of your data — see the worst offenders
A new repository called Firehound exposes AI apps leaking user data. See if anything you downloaded from the App Store is among them.
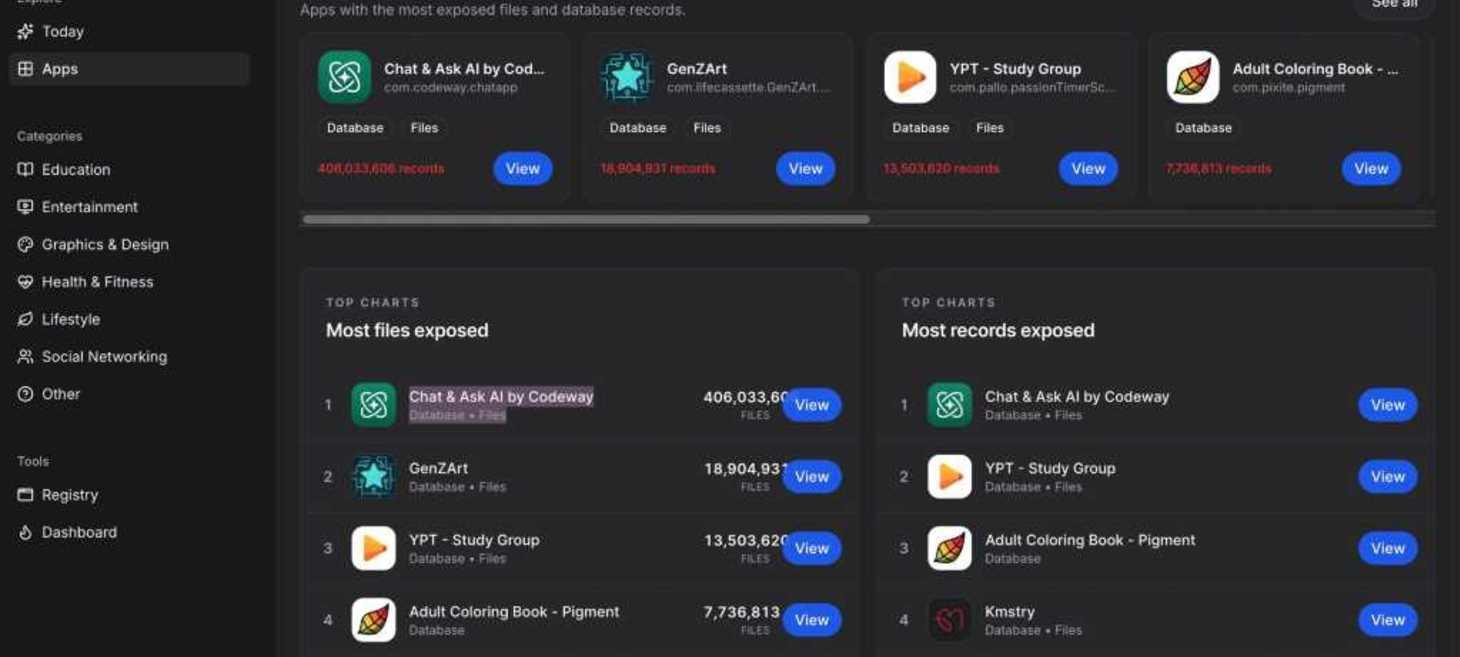
These iPhone AI apps expose your data, and they're all over the App Store
The Firehound Project is a public registry that hunts down AI apps that expose user data—and there are a ton of them.

Over 10,000 Docker Hub images found leaking credentials, auth keys
More than 10,000 Docker Hub container images expose data that should be protected, including live credentials to production systems, CI/CD databases, or LLM model keys.

New OpenAI models likely pose "high" cybersecurity risk
OpenAI says the cyber capabilities of its frontier AI models are accelerating and warns Wednesday that upcoming models are likely to pose a "high" risk, in a report shared first with Axios.