Welcome
Welcome
Hello and Welcome!
Be sure to attend our monthly meetings. Lots of good information there. Register for our Thursday October 30th Virtual Meeting on our site ISC2CT.org
Also come Join our (ISC)2 Connecticut Chapter Discord Server
Upcoming events:
Zero Trust Strategies Summit | October 8, 2025 11:00 AM ET Zero Trust is more than a marketing buzzword. As defenders look to holistic approaches to securing corporate assets, the concept of ZTNA (Zero Trust Network Access) takes on added importance to help simplify and strengthen access controls for all users, devices and data. Agenda and the Registration
Cyber Nutmeg 2025 | Friday October 10th 2025 | Central Connecticut State University CCSU Connecticut's Premier Cybersecurity Event for community anchors institutions. Join the National Guard, Connecticut Education Network (CEN), and your fellow colleagues this October. Given the current threats posed by various actors across the cyber domain, it is more imperative than ever that we ensure our vigilance and commitment to improving our cybersecurity posture across the state. The Cyber Nutmeg event is an opportunity to share our collective challenges, discuss innovative solutions, and work toward our common goal: securing our state’s networks and protecting our data. Registration Link
ISC2 Security Congress 2025| October 28-30th, 2025 | Nashville, TN + Virtual Navigate tomorrow’s threats at ISC2 Security Congress 2025. Join thousands of cybersecurity experts at the Gaylord Opryland Nashville to shape the future of the connected world. Agenda & Registration Link
Hack & Defend Summit 2025 | Tue, Oct 28 - Tue, Nov 4, 2025 | Free to Attend the Virtual Summit 12 CPEs Organizations face a critical disconnect between offensive security experts who identify vulnerabilities and defensive teams tasked with protecting systems. The Hack & Defend Summit brings these different security professionals together to learn from each other and build better protection strategies. By working together instead of separately, we can create stronger defenses against real threats. Agenda and Registration
NEACS - The NorthEast Annual Cybersecurity Summit | Thursday, November 13th 2025 | Quinnipiac University, North Haven, CT Succinct presentations will focus on topics that give cyber leaders immediately actionable insights. Moderated discussion will follow each topic, with streamlined talking points to maximize audience take-aways. Agenda focus: The intersection of academics and enterprise for cybersecurity leadersCyber industry trends with respect to vendors, investment, product sprawl for 2026 planning. Case studies from law enforcement agencies, focusing on recent trends. The convergence of fraud prevention/risk management and cybersecurity Zero Trust, what it means in the context of risk strategy vs products & services Agenda and Registration Link
Upcoming Training:
NII Certified AI Security Practitioner v2.0 (CAISP v2.0) Training Workshop | November 3rd - 6th, 2025 Online 16 CPE Credits | USD 199 (Regular participant) USD 159 (ISC2 members) We’re excited to announce our upcoming updated program, Certified AI Security Practitioner v2.0 (CAISP v2.0) training, a deep dive into AI/ML cybersecurity with enhanced focus on LLMs, secure MLOps, and emerging AI risks. Certified AI Security Practitioner v2.0 (CAISP v2.0) training, builds on the foundation by diving deeper into technical, practical, and hands-on aspects of AI/ML security. It introduces advanced topics such as adversarial testing, secure MLOps, agentic AI, jailbreak attacks, and governance standards (ISO 42001, NIST AI RMF, OWASP LLM Top 10). With more case studies, and real-world simulations, participants gain practical skills in testing, securing, and governing AI/ML systems in enterprise environments Registration
NII ISO 42001 Lead Auditor Training (Exemplar Global, USA Certified) | November 17th - 19th 2025 8AM-3PM EST Online 21 CPE Credits | Regular Participant - USD 799 | ISC2 Member/Clients -USD 699 | Early Bird Discount (registering before 15 Oct 2025)- USD 575 The course intends to equip participants with the skills and knowledge required to understand how an AIMS is implemented based on Annex B of ISO/IEC 42001:2023, lead Artificial Intelligence audits effectively, ensuring compliance with ISO 42001:2023. It will cover audit planning, execution, and reporting while emphasizing risk management, governance, and continual improvement Registration
Thank you to our Sponsors
Quinnipiac University is committed to helping advance the field of cybersecurity through its School of Computing & Engineering. To support the growth of professionals within cybersecurity and computing, Quinnipiac offers flexible online and on-campus opportunities that deliver practical skills you can immediately apply on the job. Both its MS in Cybersecurity and MS in Computer Science programs feature hands-on experience in lab settings that simulate real-world scenarios. To learn more about these exciting opportunities, Visit Quinnipiac University
Cyber News

California Gov. Gavin Newsom Signs Bill Creating AI Safety Measures
California law aims to enhance online safety by installing guardrails on the development of frontier artificial intelligence (AI) models.

CISA Sounds Alarm on Critical Sudo Flaw Actively Exploited in Linux and Unix Systems
CISA adds critical Sudo flaw CVE-2025-32463 and four other exploited vulnerabilities to KEV list.

First Malicious MCP Server Found Stealing Emails in Rogue Postmark-MCP Package
Malicious npm postmark-mcp v1.0.16 backdoored MCP server stole emails from 1,643 downloads.
AI-powered vulnerability detection will make things worse, not better, former US cyber official warns
Patching won’t be able to keep up with discovery, said Rob Joyce, who once led the National Security Agency's elite hacking team.
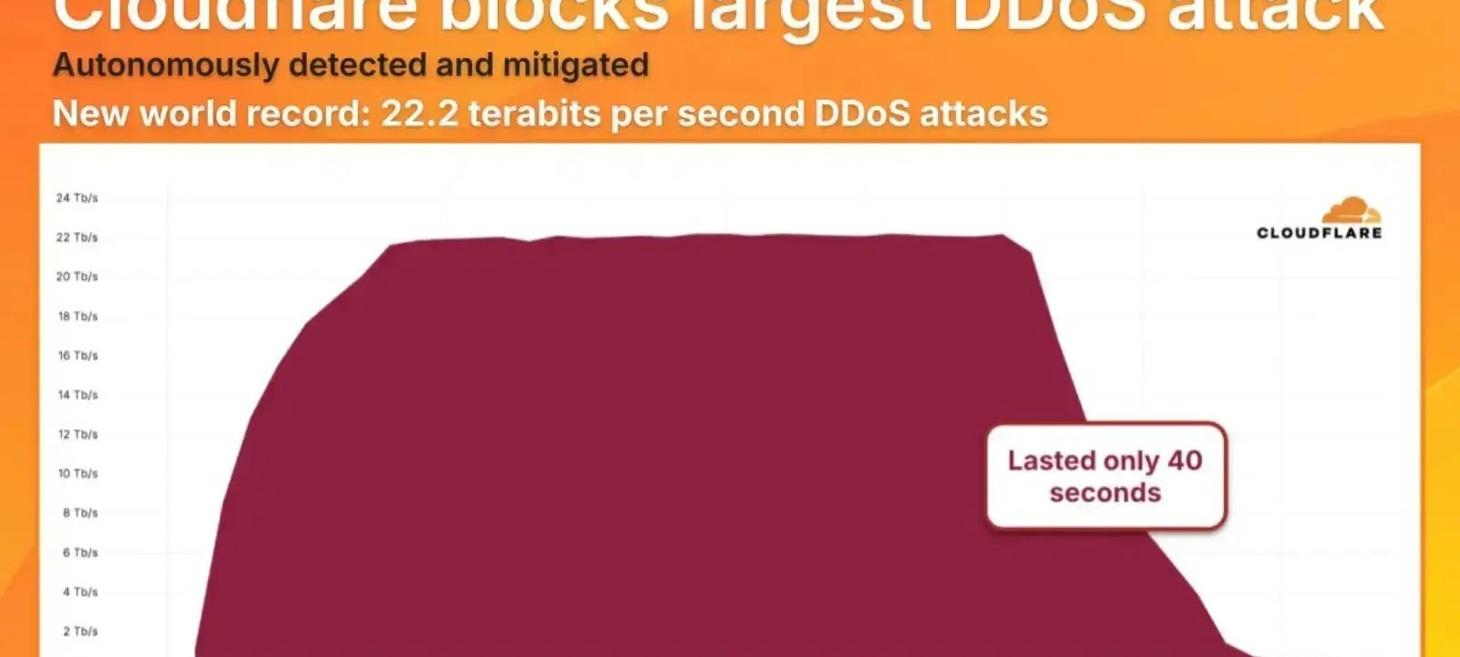
22.2 Terabit-Per-Second DDoS Attack Establishes New Global Record
This event more than doubles the size of the previous record-setting UDP flood, which reached 11.5 Tbps and lasted 35 seconds.

Nearly 50,000 Cisco firewalls vulnerable to actively exploited flaws
Roughly 50,000 Cisco Adaptive Security Appliance (ASA) and Firewall Threat Defense (FTD) appliances exposed on the public web are vulnerable to two vulnerabilities actively leveraged by hackers.

What to do if your company discovers a North Korean worker in its ranks
U.S. businesses face complex legal, cybersecurity, and compliance challenges after uncovering North Korean IT workers on their payrolls, experts warn at Google's Cyber Defense Summit.

Shai-Hulud Worm NPM Supply Chain Attack
RL researchers have detected the first self-replicating worm compromising popular npm packages with cloud token-stealing malware.

'Trifecta' of Google Gemini Flaws Turn AI Into Attack Vehicle
Flaws in individual models of Google's AI suite created significant security and privacy risks for users, demonstrating the need for heightened defenses.

Npm Package Hides Malware in Steganographic QR Codes
Attackers have poisoned a code package on the npm registry in a novel way, hiding credential-stealing malware in steganographic QR codes embedded in a package

Top Zero-Day Vulnerabilities Exploited in the Wild in 2025
The cybersecurity landscape in 2025 has been marked by an unprecedented surge in zero-day vulnerabilities actively exploited by threat actors.
